
The Future of Customer Loyalty in 2023 & Beyond
Gain valuable insights from leading experts on the top 11 loyalty trends.
As consumers in today’s digital world, we share huge amounts of personal data. We enter our age and credit card number when we register for an online service. We allow companies to track what we click on and buy. We broadcast our geographical location.
From a brand’s perspective, data has never been more critical to driving business growth and building a strong base of loyal customers. Today’s consumers willingly share their data in exchange for a better, more personalized experience. In doing so, they’re trusting brands to keep their data safe and secure.
This guide explores some important distinctions between key security and privacy terms, and looks at why security and privacy are essential for both brands and consumers. We’ll also share some important security, privacy, and data management best practices. And, finally, we’ll discuss how a loyalty program can help brands make significant strides in both privacy and personalization.
There’s no legal definition of data privacy, however, according to Integrate.io, it usually refers to the handling of critical personal information, also called “personally identifiable information” (PII) and “personal health information” (PHI). This can include social security numbers, health records, and financial data. For organizations, data privacy extends beyond employee and customer personal data to include information about the company’s operations—such as research and development, and company financials.
The term “handling” refers to the proper collection, handling, transfer, storage, utilization, sharing, and management of personal data. Companies must take proper measures to ethically and legally handle consumer data, referred to as data governance, to ensure this data doesn’t end up in the wrong hands and complies with data privacy laws that vary across countries. The European Union’s General Data Protection Regulation (GDPR) wasn’t the first data privacy law but it certainly was groundbreaking and the most comprehensive in addressing today’s digital-first data landscape.
Many people use the terms data privacy and data security interchangeably but there’s a clear distinction between the two. Both are essential for earning and maintaining customer trust.
Branch or subset of data security
Focuses on the rights of individuals
Revolves around compliance with data protection laws & regulations
Focuses on how to collect, process, share, archive and delete data ethically and legally
Standards and safeguards an organization takes to prevent any third party from unauthorized data access or any unintentional alteration, deletion or disclosure of data
Focuses on protection of data from internal and external threats and prevents the exploitation of stolen data, as in the case of a data breach or cyber attack
Includes access control, encryption, tokenization, hashing, network security, etc.
A prerequisite for data privacy
While consumers willingly share data in exchange for brands using it to deliver a personalized experience, they want to know who’s using their data, how and why. Many data privacy regulations include specific provisions that empower consumers with the right to request their data be updated, deleted and more.

86% of U.S. citizens have attempted to remove or decrease their digital footprint online.
(Source: Pew Research Center)
Organizations that fail to comply with today’s growing list of country-specific data privacy regulations will face steep penalties. Fines for not being compliant with regulations such as GDPR have risen by 113% over the past year. Data privacy research from the Kellogg School of Management at Northwestern University predicts regulators could impose liability fines on companies whose data were leaked, with the amount reflecting the extent of user harm. But losing consumers’ trust is even more impactful to a company’s bottom line.
“To increase customer trust, executive leaders need to build a holistic and adaptive privacy program across the organization, and be proactive instead of responding to each jurisdictional challenge.”
Bart Willemsen, Vice President Analyst, Gartner
Back in 2020, Gartner Vice President Analyst Bart Willemsen predicted privacy-first products would follow the likes of ‘organic’ and ‘cruelty-free’ in becoming a reason for consumers to purchase products—and he was right.
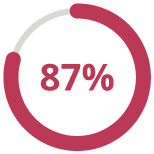
87% of consumers said they would not do business with a company if they had concerns about its security practices.
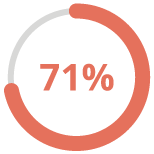
71% of consumers said they would stop doing business with a company if it gave away sensitive data without permission.
(Source: McKinsey & Company)
There’s a reason data is equated to oil. It’s the lifeblood of every business, greasing the wheels of CRMs, ESPs, CXs, mobile, loyalty and every other customer-focused platform on the planet. The more data you have about your customers, the better the experiences you can deliver. So companies are collecting a LOT of data.
Using data to run, track and control businesses has been around longer than you think. According to Wikipedia, the earliest records date back 7,000 years to record the growth of crops and herds. Marketers have been on the quest for customer data to take their businesses to the next level and drive personalization efforts for decades. Starting in the 1980s, the internet, online advertising and ecommerce really shifted data collection into high gear.
The mindset was the more data, the better, and companies weren’t sure exactly what data was really necessary or useful. This unchecked practice led to the term ‘Big Data’ coined in 2005. The data primarily captured events that had already happened, such as a completed sale, rather than analyzed to gain insights and predict future behaviors or events.
Fast-forward to the Internet of Things (IoT) and the acceleration of digital transformation plans forced by the pandemic, and we’re now looking at an exponential increase in customer data that companies have to secure and manage.
“There were 5 Exabytes of information created between the dawn of civilization through 2003, but that much information is now created every 2 days, and the pace is increasing.”
Eric Schmidt, Former CEO of Google
According to the Harvard Business Review, our new data economy won’t tolerate this kind of reckless data collection and management. They advise that any organization that generates any value from personal data changes the way they acquire it, share it, protect it and profit from it.
Turns out, you can have too much of a good thing. The data free-for-all of the past decade has come to an end as consumers have realized how much data companies are collecting without a clear understanding of why or what’s being done with it. The net result has been consumers are now much more aware that their data was being stored and used in ways they didn’t approve of.

Americans are not feeling in control of their digital lives. 81% report they felt little to no control over their data.
(Source: Pew Research Study)
Gartner reported a decline in customer satisfaction beginning in 2019. This downward trend has continued as consumer trust has eroded, in large part due to their concerns around privacy. Uncertainty about how their information is being used and shared has consumers on edge. Now, more than ever, data-driven marketers must be extra diligent to ensure they have effective security, privacy, and data management practices—and show consumers they can be trusted with their data.
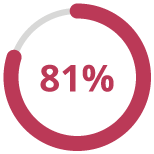
81% of consumers said they need to trust a brand to buy from them.
(Source: 2019 Edelman Trust Barometer Special Report)
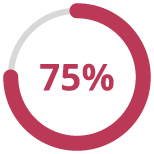
75% of customers won’t even consider buying a product if they have doubts the company will keep their personal data safe and private.
(Source: IBM cybersecurity study)
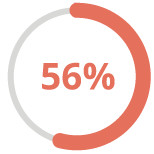
56% of consumers don’t trust brands to protect their data.
(Source: Acquia)
The majority of companies are sitting on a ton of customer data that isn’t necessarily secure and wasn’t collected with the consumers’ consent. They don’t have a good handle on all the privacy regulations they need to comply with. And, they don’t have good processes in place to effectively manage that much data. This guide is intended to help organizations effectively improve their capabilities around all three of these important business requirements.

KPMG performed two surveys in 2021. The first was to 2,000 U.S. adults, the second to 250 decision-makers involved with security, privacy and data at companies with 1,000+ employees. The results, which they shared in a report named “Corporate Data Responsibility: Bridging the Trust Chasm,” highlight the still-significant gap in how each of these groups view these important topics.
86% said they feel a growing concern about data privacy
78% expressed fears about the amount of data being collected
40% don’t trust companies to use their data ethically
47% said they’re concerned about their data being hacked
51% were worried about their data being sold
70% expanded their collection of consumer data over the past year
75% said they’re comfortable with the level of data their company collects
75% said they’re comfortable with the level of data their company collects
“This split between business and consumer sentiment isn’t new, but its persistence shows that businesses have a long way to go if they want to make the public more comfortable with how they are collecting, using and safeguarding data. Failure to bridge this divide could present a real risk of losing access to the valuable data and insights that drive growth.”
Orson Lucas, U.S. Privacy Services Leader, KPMG
Good security and data privacy practices build trust and long-term relationships with customers. And they demonstrate to your customers that you care about protecting them and their data. This can translate into a powerful differentiator.
KPMG contends that companies that take the lead in establishing responsible security and data privacy practices will be glad they made the investment. Based on their research, consumers want companies to take the lead in collecting and using data responsibly, and educating them on how to protect their own data.
“Our research has provided insights into how individuals want businesses to handle their personal data. Companies that take the lead on this issue—by demonstrating that they are hearing what consumers are saying and taking meaningful action—will be positioned to reap the ongoing benefits of access to consumer data.”
Martin Sokalski, Principal, Emerging Technology Risk Practice, KPMG
While good security and data privacy standards and practices may be time-consuming and challenging, they can also pay off. Consumers will reward companies that make protecting them a priority. According to McKinsey & Company, many companies are adding consumer privacy to their value propositions and aligning their privacy policies messages and cookie notices with the overall brand.

“As users become more and more aware, they start to choose companies based on whether the companies are preserving privacy. Companies should actually embrace this because this might become a competitive edge.”
Ruslan Momot, Visiting Assistant Professor of Operations, Kellogg
Ruslan Momot, a visiting Assistant Professor of Operations at Kellogg believes improving privacy measures will not only help organizations comply with data privacy regulations, it’ll also help them bring in more business.

Consumers have more control than ever over who they share their personal data with. And everything is moving in the direction of giving them more, not less, power— whether through legislative routes like GDPR or CCPA which protect and enhance consumer privacy, or technology shifts that can be seen in Apple’s updates, that give users unprecedented control over the data they share, and with whom.
Alongside these external developments, it’s safe to say consumers are also developing a better general awareness of their ability to opt out of receiving marketing from brands. They’re far less tolerant of poor experiences and irrelevant messaging.
While it might be tempting to see this as a challenge, fundamentally this evolution is a good thing because it creates a better value exchange. For too long, brands have been abusing the ability to batch and blast messages into people’s lives without considering whether they want them or not. Now, increasingly, brands must demonstrate that they’ll give the consumer an amazing experience in return; an experience that makes use of the data that their customers share.
We surveyed 2,000 U.S. consumers at the end of last year and found that 70% of those surveyed have no objection to sharing personal information if it results in a better experience. This clearly highlights that brands who offer their customers a highly personalized, relevant experience will have no issues collecting personal data from their customers because they’re using the insights to improve their experience.
So while brands might fall foul of a hefty fine if they do not adhere to the privacy regulations they’re faced with, it’s not the only way to misstep. Ultimately if companies don’t adapt their approach to align with consumers’ increasing expectations of a better experience, using the data they have elected to share, then they will struggle long-term to attract and keep their customers based on the experiences they offer.
When it comes to buttoning up security, there are many considerations. Here’s a summary of some of the key factors you need to protect you and your customers from internal and external threats.
Demonstrate you have all the necessary security protocols in place to safeguard your customers’ data. Here are a few of the main certifications.
ISO/IEC 27001 is an international standard for how to manage information security. The standard was originally published jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) in 2005, then revised in 2013. It details requirements for establishing, implementing, maintaining, and continually improving an information security management system (ISMS)—the aim of which is to help organizations make the information assets they hold more secure.
ISO/IEC 27001 requires that management:
Systematically examine the organization’s information security risks, taking account of the threats, vulnerabilities, and impacts
Design and implement a coherent and comprehensive suite of information security controls and/or other forms of risk treatment (such as risk avoidance or risk transfer) to address those risks that are deemed unacceptable
Adopt an overarching management process to ensure the information security controls continue to meet the organization’s information security needs on an ongoing basis
The SOC 2 Type 2 audit is based on criteria used to evaluate controls relevant to the security, processing integrity, availability, confidentiality and privacy of any system. The SOC 2 Type 2 report includes audit details of the service organization controls outlined by the Trust Services Criteria (TSC) set by AICPA.
Specifically, the SOC 2 Type 2 audit covers:
Some other areas specifically analyzed under a SOC 2 Type 2 audit include:
Common risks include virus attacks and malicious threats through websites and applications. One click is enough to put your data at risk. Make sure all your applications are properly vetted and have every possible security protocol in place.

Data quality & quantity
Avoid collecting unnecessary and irrelevant information. Respond promptly to individuals’ requests to correct or delete their personal information.

Personnel & staff
The personnel dealing with data collection, storage and management need to be sufficiently trained. Any irresponsible move can threaten the privacy of individuals as well as the company’s integrity, reputation and safety.

Disaster recovery & breach response
Companies need to be fully prepared for mishaps like data breaches and other threats. A swift breach response protocol will ensure the situation is handled responsibly and with due diligence.

Protecting data at rest or in motion
Ensure data is protected both at rest and in motion. Also, know how long data is available to use.
Establishing legal and ethical data privacy practices is critical to ensuring your customers’ have confidence you’re protecting them and their personal information. Here are some initial steps you can take to establish and promote good data privacy policies across your organization.
Chances are you have a lot of data—from different sources, in different formats, and not all of it useful or being leveraged for any business value. Look at what data you currently have that you can delete and be more thoughtful and intentional about the data you collect moving forward.
Take steps to ensure your data privacy policy is easy to understand. Explain to customers how you collect data and use it for their benefit. Be sure to be specific about the value you’ll deliver in return.
“The best data use disclosures are thorough, well-organized, and easy to understand. They show consumers who is using their data and how, and draw a clear connection between the business use case and benefit to the consumer.”
Rob Fisher, U.S. Impact Leader, KPMG
Just as effective marketing requires data scientists and analysts, effective data privacy requires professionals, such as Data Privacy Officers or Data Protection Officers, that are specifically trained to oversee data policy across your entire organization.
Your customers want to know about and control how their data will be used. You need to make it easy for them to modify preferences with easy-to-use tools. Read more about how giving customers options can go a long way to building trust and loyalty.
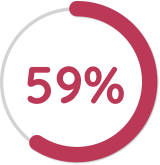
59% of companies give customers control over how much data goes to whom.
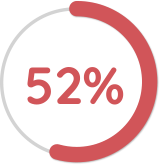
52% of companies allow people to opt out of sharing data.
(Source: KPMG)
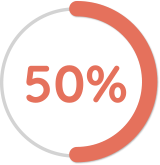
50% of companies let customers view personal data that’s been collected about them.
IDC recommends companies look at a new software category called ‘data privacy management’. It grew 46% in 2021 and provides tools to manage customer personally identifiable information (PII) as well as enabling customers to control and delete their data.
When it comes to complying with data privacy regulations, Gartner Vice President Analyst Bart Willemsen has this advice. “People are actively demanding privacy protection, and legislators are reacting. If your organization operates globally, focus on standardizing operations in accordance with the GDPR, and then adjust as required for local requirements.”
“I like to use the term ‘data etiquette,’ because it’s about more than just following local laws. For me, data etiquette means collecting and using data in a way that is ethical and respectful.”
Jodi Alperstein, Vice President and General Manager, Twilio
Annex Cloud partner Twilio’s Vice President and General Manager, Jodi Alperstein, advises that many businesses find investing in data quality improves trust in their data, reduces time spent by engineering and business teams navigating and validating data, and ultimately allows a business to grow faster. She recommends companies identify the data they want versus the data they need, then only use the latter to build winning customer engagement.
An article by McKinsey & Company summarizes their findings after surveying 1,000 consumers in North America. The research shows companies can differentiate themselves by taking deliberate measures around security and data privacy.
McKinsey recommends organizations take these proactive measures:
Data mapping
Perform data mapping to categorize the types of data you collect from customers. Learn more about data types and collection tips.
Collection
Know what data you actually need and limit collection based on the essentials.
Policies
Update data storage and security policies to account for each category of data.
Access
Define identify- and access-management practices based on roles and data categories.
Response
Put your breach/crisis response processes to the test to ensure they’ll hold up under pressure.
Automation
Define clear, standardized procedures to govern request for the remove or transfer of data and, if possible, automate them.
Storage
Work with third parties, affiliates and vendors to understand how and where data is stored.
Infrastructure
Reduce the number of systems used for data storage to reduce risk.
Applications
Build privacy into customer-facing apps, including features like automatic timed logouts and strong password requirements.
Transparency
Clearly communicate to customers when and why their data is being collected.

In this privacy-regulated environment, problems arise when businesses collect data from third-party sources like data brokers. The origin of the data and the consent status is ambiguous, and businesses are asking for regulatory fines when using this data. So the best way for businesses to deliver personalization and protect customer privacy is to move away from third-party data and rely on zero party data.
One thing we need to understand is that customers crave personalization and they’re ready to pay a premium and give up additional data to get that personalized experience on their buying journey.
If businesses are transparent and upfront with their purposes and limit themselves to those purposes, customers will be more open towards and proactively share information about their preferences. This is a core tenet of everything we do at Zoho CRM, and we aim to empower our customers to do the same with our products.
Since it comes directly from your customers, zero-party data is more reliable, accurate and relevant. You also end up saving on expenses that would otherwise be spent on data brokers or data aggregators to buy similar data. The most important aspect of zero-party data is that you know exactly when, how, and why the data was collected, along with customer consent to ensure that you still adhere to all the security and privacy regulations while delivering personalized information.
Good data management practices, also known as data governance, is essential for organizations to not only comply with regulations but also maintain consumer trust. For many organizations, this will require a major shift in how they collect, share, transfer and manage consumers’ data.
According to Harvard Business Review (HBR), their research and experience indicate the new data economy will require organizations to reorganize their data operations around the new fundamental rules of consent, insight, and flow.

Rule 1: Trust over transactions
The days of gathering as much data as possible—often without the customers’ knowledge or consent—are over. According to HBR, data collected with meaningful consent will soon be the most valuable data of all and the only data companies will be permitted to act upon. Brands need to offer their customers options for sharing their data. The more robust and thorough your consent practices are, the more valuable your customer database becomes.
Rule 2: Insight over identity
Skip the third-party data agreements that compromise both security and privacy. Moving forward, opt for newer technologies that enable insights without having to acquire or transfer data. Also, use algorithms that exchange non-identifying statistics. For example, Dspark cleans, aggregates and anonymizes more than one billion mobile data points every day, delivering insights on everything from demographics to shopping without selling or transferring the data.


Rule 3: Flows over silos
If you’re collecting data with meaningful consent and acquiring insights without transferring data, you’ll be able to resolve that internal conflict between CIOs trying to keep data under lock and key while CDOs and CMOs try to let it run wild. When internal teams work together toward adding value to customers, it’s a win-win. For example, a bank’s mortgage team gains a customer’s consent to share their new address with service providers such as moving companies, utilities, and internet providers. Acting as a middleman with the customer’s permission, the bank can serve up personalized offers and services, and notify providers of address changes and move-in dates, relieving the customer of burdensome moving chores.

Establishing and maintaining trust is essential for platforms and products to safely leverage sensitive data, including customers’ personal data. Here are a few concepts that explain how data governance can enable trust.
From the customer’s perspective, brands need to think about several factors that contribute to establishing trust:
A product’s ability to provide meaningful value that’s easy to recognize.
Consistent delivery of a capability in a manner that meets the quality standards according to the user’s expectations.
The belief that the trusted party wants to do good for the user, including a description of benefits to the user resulting from their relationship with the product and benefits to the provider.
All three of these factors should be considered when attempting to establish trust with your customers.
Another way of thinking about trust is from the standpoint of authority. For example, trust is established when an authority reliably enforces policy. Whether it’s a computer system trusted by a user or a government trusted by a citizen, the individual feels safe to be in that environment because harmful and unauthorized activities are controlled by rules that are consistently applied (i.e., in computing, we call these rules “policies”). Stated another way, we trust that a system is safe when all reasonably foreseeable harms have been identified and controlled via the consistent enforcement of policy. For a system to remain trusted, it must be governed in a manner that ensures the ongoing effectiveness of these controls. These controls can be administrative (e.g., written business rules, procedures etc.), technical (e.g., computer logic based on business rules, encryption, role-based access controls, etc.) or physical (e.g., a secure data center that requires badged access etc.).

In practical terms, this means that someone, somewhere is responsible for overseeing these policies and controls. From a governance perspective, this means that roles must be established and delegated with responsibility, authority and accountability for controls. This responsibility will include things like ensuring requirements are defined, understood and implemented. This responsibility should be captured in a formal document, like a charter or an operating model that’s made available to all users of the system. From a data governance perspective, this often starts with identifying the roles that manage data identified as high value or high risk.
To earn users’ trust, organizations must be able to clearly communicate capabilities and reliability, and deliver those capabilities according to some quality standards. Providers must balance the need for user understanding against any increased security risk arising from too much transparency into the inner workings of their systems. In regulated industries, the government’s role is to ensure policies are developed, with opportunity for public input and in compliance with regulations.
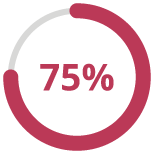
75% of consumers said they want great transparency about how their data is used.

40% of consumers said they’d share data if they knew how it would be used and by whom.
(Source: KPMG)

53% of companies have actively tried to show how consumer data is used.
This guide shares many proof points supporting the fact that today’s consumers demand both personalization and privacy. These two often seem to be conflicting goals. So, how do brands manage to do both? Here are some helpful tips from a few Annex Cloud partners.

71% of U.S. consumers expect personalization, with 76% admitting they get frustrated when they don’t get it.
(Source: McKinsey & Company)
Every company must balance privacy and value. Customers are willing to give up their data if they receive something of value in return. Here are a few examples of brands that are getting it right.
Topics API, a technology adopted by Google, uses Internet-Based Advertising (IBA) that enables businesses to collect data based on customers’ online activities and searches. Utilizing only the top five customer searches and limiting data accessibility to just three weeks makes it hard to accurately locate and identify customers, protecting customer identity.
Gatorade’s Gx platform tests how each customer sweats in order to provide relevant sports fuel recommendations. The Gx Sweat Patch provides information based on perspiration and categorizes customers to deliver personalized experiences.
Spotify uses Collaborative Filtering that creates a unique identity for every user, based on the content they consume. It segments customers into categories and shows them relevant ads and content options.
(Ad Age)
According to a Boston Consulting Group study, businesses that are able to deliver personalized experiences to customers across the customer journey achieve cost savings of up to 30% and revenue increases up to 20%. Loyalty programs are designed to personalize and add value to every customer interaction, and the data these programs collect are shared with the customer’s consent. This zero-party data is accurate since it comes directly from the source and enables the personalized experiences today’s consumers crave.
“If you want to make your customer experiences as personalized as possible, you first have to make them as positive as possible. The more value you can provide with each experience, the more open customers are to providing the kind of data you need to make their experiences more personalized, creating that beautiful upward spiral.”
Jay Weinberg, Co-founder and Partner, Ascendant Loyalty Marketing
Having a clear vision for your loyalty program, as well as clear goals, helps ensure you only collect essential data from your customers. Loyalty programs provide a mutual value exchange that provides on-going opportunities to clearly communicate what your customers’ data will be used for and the value they’ll receive as a result of sharing their data. This transparency builds trust and encourages on-going engagement, while also increasing retention and repeat purchases.
Not all loyalty vendors enable the same level of personalization, nor commit to the highest levels of security and privacy standards. Our Guide to Choosing the Right Loyalty Vendor outlines the key factors and features to make sure you evaluate before making a decision.
Annex Cloud’s enterprise-ready loyalty solution is designed to make sure you have all the bases covered when it comes to security, privacy, data management and personalization. Our 125-plus integrations make sure you know your customers no matter how they’re engaging with you.